Nearly a decade-long cyber espionage group that targeted a variety of Eastern European governments and security-related organizations including the North Atlantic Treaty Organization (NATO) has been exposed by a security research firm.
The US intelligence firm FireEye released its latest Advanced Persistent Threat (APT) report on Tuesday which said that the cyber attacks targeting various organisations would be of the interest to Russia, and "may be" sponsored by the Russian government.
The Report entitled "APT28: A Window Into Russia's Cyber Espionage Operations" published by FireEye has "evidence of long-standing, focused operations that indicate a government sponsor - specifically, a government based in Moscow."
"Despite rumours of the Russian government's alleged involvement in high-profile government and military cyber attacks, there has been little hard evidence of any link to cyber espionage," Dan McWhorter, FireEye vice president of Threat Intelligence, wrote in a blog post discussing the report.
"FireEye's latest APT report sheds light on cyber espionage operations that we assess to be most likely to be sponsored by the Russian government, long believed to be a leader among major nations in performing sophisticated network attacks."
The cyber-espionage group believed to have been operating since at least 2007 in order to steal political and state secrets from businesses and foreign governments. The group launched a cyber attack on government in Georgia, Eastern Europe, as well as NATO and the Organisation for Security and Co-operation in Europe, according to the report.
Whereas the Russian cyber criminal groups are known for conducting massive cyber campaigns aimed at stealing money and financial information, but APT28 focuses on "privileged information related to governments, militaries and security organizations."
“This group, unlike the China-based threat actors we track, does not appear to conduct widespread intellectual property theft for economic gain,” FireEye stated in the report. “Nor have we observed the group steal and profit from financial account information.”
The security firm analyzed that the malware used by APT28 features a consistent use of the Russian language. Moreover, more than 96 percent of malware samples analyzed by the researchers were compiled between Monday and Friday, between 8AM and 6PM in the time zone paralleling working hours in Moscow and St. Petersburg. This regularity in the work suggests that the hackers were in Moscow, the report argues.
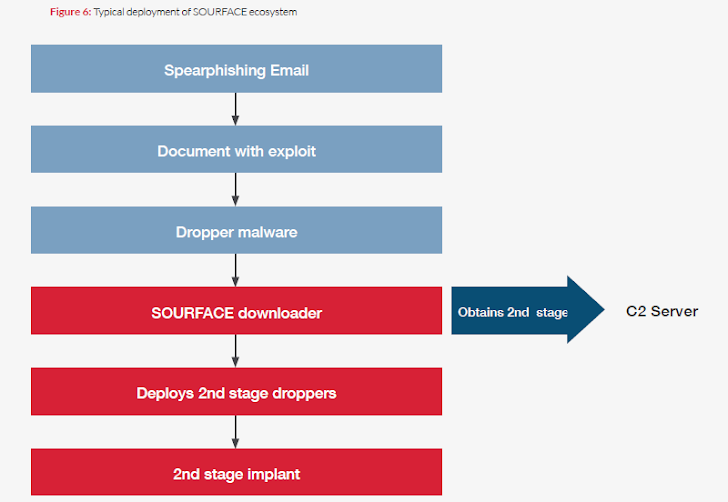
The APT28 group has constantly updated their software and made the resulting binaries difficult to reverse engineer. It used a downloader tool that FireEye dubbed "SOURFACE", a backdoor labelled "EVILTOSS" that gives hackers remote access and a flexible modular implant called "CHOPSTICK" to enhance functionality of the espionage software.
Infection is usually achieved via a spear phishing email with a relevant lure and the malware hidden in the attachment. The hacker group has also created a number of fake domains for UK-based defence events, including the Counter Terror Expo, as part of the operation to gather intelligence on attendees.
Together with the help of above mentioned tools, the group gained access to the file system and registry; enumerate network resources; create processes; log keystrokes; access stored credentials; execute shellcode, and encrypt exfiltrated data uploaded with an RSA public key.
Together with the help of above mentioned tools, the group gained access to the file system and registry; enumerate network resources; create processes; log keystrokes; access stored credentials; execute shellcode, and encrypt exfiltrated data uploaded with an RSA public key.
“The coding practices evident in the group’s malware suggest both a high level of skill and an interest in complicating reverse engineering efforts,” the report stated.
In another report , a top White House official has confirmed that Russian hackers have hacked into the unclassified White House computer networks. "we identified activity of concern on the unclassified Executive Office of the President network,".
Russia has been suspected of attacks on Ukraine too, including attempts to gain access to politicians’ mobile phone communications.